
🛎️ Access
php로 작성된 페이지입니다.
알맞은 Id과 Password를 입력하여 플래그를 획득하세요.
플래그의 형식은 DH{…} 입니다.
👾 Exploit Algorithm & Payload
> index.php
<html>
<head>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.2/css/bootstrap.min.css">
<title>Type c-j</title>
</head>
<body>
<!-- Fixed navbar -->
<nav class="navbar navbar-default navbar-fixed-top">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="/">Type c-j</a>
</div>
<div id="navbar">
<ul class="nav navbar-nav">
<li><a href="/">index page</a></li>
</ul>
</div><!--/.nav-collapse -->
</div>
</nav><br/><br/><br/>
<div class="container">
<div class="box">
<h4>Enter the correct ID & Password.</h4>
<p>
<form method="post" action="/check.php">
<input type="text" placeholder="Id" name="input1">
<input type="text" placeholder="Password" name="input2">
<input type="submit" value="제출">
</form>
</p>
</div>
<?php
require_once('flag.php');
error_reporting(0);
?>
</div>
</body>
</html>> check.php
<html>
<head>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.2/css/bootstrap.min.css">
<title>Type c-j</title>
</head>
<body>
<!-- Fixed navbar -->
<nav class="navbar navbar-default navbar-fixed-top">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="/">Type c-j</a>
</div>
<div id="navbar">
<ul class="nav navbar-nav">
<li><a href="/">Index page</a></li>
</ul>
</div><!--/.nav-collapse -->
</div>
</nav><br/><br/><br/>
<div class="container">
<?php
function getRandStr($length = 10) {
$characters = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ';
$charactersLength = strlen($characters);
$randomString = '';
for ($i = 0; $i < $length; $i++) {
$randomString .= $characters[mt_rand(0, $charactersLength - 1)];
}
return $randomString;
}
require_once('flag.php');
error_reporting(0);
$id = getRandStr();
$pw = sha1("1");
// POST request
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$input_id = $_POST["input1"] ? $_POST["input1"] : "";
$input_pw = $_POST["input2"] ? $_POST["input2"] : "";
sleep(1);
if((int)$input_id == $id && strlen($input_id) === 10){
echo '<h4>ID pass.</h4><br>';
if((int)$input_pw == $pw && strlen($input_pw) === 8){
echo "<pre>FLAG\n";
echo $flag;
echo "</pre>";
}
} else{
echo '<h4>Try again.</h4><br>';
}
}else {
echo '<h3>Fail...</h3>';
}
?>
</div>
</body>
</html>
#1
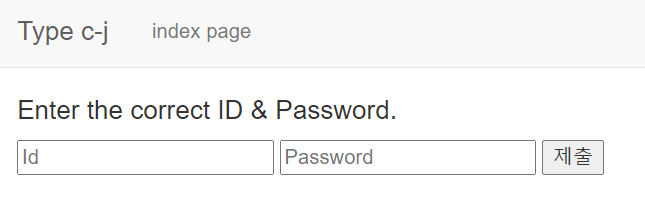
: '/' 페이지에서 id와 password를 입력 후 제출하면 값을 확인할 수 있을 것으로 예상된다.
: 그러나 어떤 값을 입력하여도 "Try again."이라는 결과가 출력되어서 코드를 분석했다.
#2
...
$id = getRandStr();
$pw = sha1("1");
...
: id는 getRandStr() 함수를 분석하면 될 것으로 보인다.
: pw는 sha1 함수는 SHA-1 16진수 40자리로 렌더링되는 암호화 해쉬 함수로 보인다.
function getRandStr($length = 10) {
$characters = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ';
$charactersLength = strlen($characters);
$randomString = '';
for ($i = 0; $i < $length; $i++) {
$randomString .= $characters[mt_rand(0, $charactersLength - 1)];
}
return $randomString;
}
require_once('flag.php');
error_reporting(0);
$id = getRandStr();
$pw = sha1("1");
// POST request
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$input_id = $_POST["input1"] ? $_POST["input1"] : "";
$input_pw = $_POST["input2"] ? $_POST["input2"] : "";
sleep(1);
if((int)$input_id == $id && strlen($input_id) === 10){
echo '<h4>ID pass.</h4><br>';
if((int)$input_pw == $pw && strlen($input_pw) === 8){
echo "<pre>FLAG\n";
echo $flag;
echo "</pre>";
}
} else{
echo '<h4>Try again.</h4><br>';
}
}else {
echo '<h3>Fail...</h3>';
}
: 분석 결과 if((int)$input_id == $id && strlen($input_id) === 10), $input_id는 (int)를 통해 정수로 형변환 된 후에 $id와 비교되고, 길이는 10이다.
: 여기서 PHP 에서의 연산자 취약점 '==' 이 취약할 수 있다는 것을 알 수 있다.(Loose Comparison)
: '==' 연산자는 PHP문에서 $a와 $b가 같으면 true, '===' 연산자는 $a와 $b가 같고, 동일한 자료형일 시 true
: 즉, '==' 연산자는 문자열과 정수를 비교했을 때, 문자열이 정수(int) 혹은 실수(float)으로 바뀌게 된다.
🔑Analysis and results for obtaining the Flag DH{…}
// 길이 10
// 0e 뒤로 숫자 랜덤하게 가능
// 문자열을 정수로 형 변환할 때는 문자열의 앞 부분부터 숫자가 아닌 문자를 만날 때까지 숫자를 추출하여 변환
(int) $input_id = 0e12345678 → 0 * ... → 0
(int) $input_id = 0e1234567a → 0 * ... → 0
...
: 이를 활용해 매직해쉬(0e: 이것으로 시작하는 문자열 뒤가 모두 숫자면 float형태로 인식한다)를 '==' 연산자와 함께 적용할 경우 취약할 수 있다.
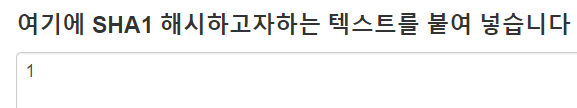
// 길이 8
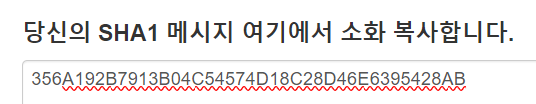
$input_pw = 356A192B
: $pw의 경우는 https://www.convertstring.com/ko/Hash/SHA1 해당 사이트에서 SHA-1 해시하고자 하는 텍스트인 "1"을 입력하였더니 "356A192B7913B04C54574D18C28D46E6395428AB" 다음과 같은 결과가 나왔다.


'[Dreamhack]WebHacking > Wargame&CTF' 카테고리의 다른 글
| [Dreamhack] Level1:Beginner blue-whale (1) | 2024.02.07 |
|---|---|
| [Dreamhack] Level2: Dream Gallery (0) | 2024.02.03 |
| [Dreamhack] Level2: filestorage (0) | 2024.02.02 |
| [Dreamhack] Level1: baby-union (2) | 2024.02.02 |
| [Dreamhack] CTF Season 5 Round #2 - php7cmp4re (0) | 2024.01.28 |



